Cloud Security Best Practices: Protecting Your Applications in 2024
Essential security measures every development team should implement when deploying applications to cloud platforms.
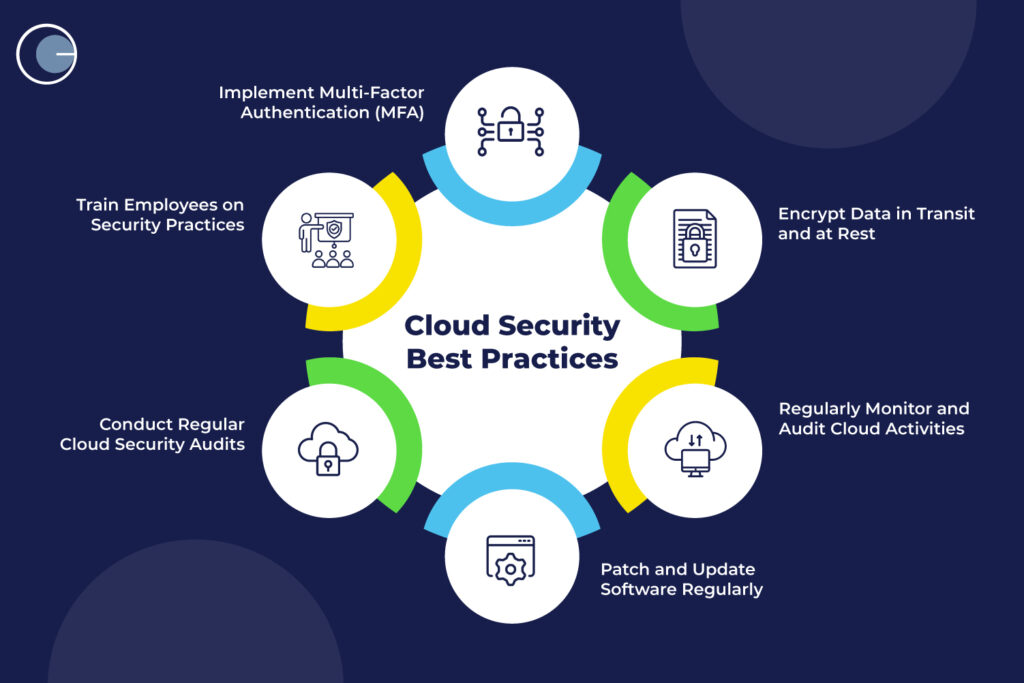
The Cloud Security Imperative
As more businesses move to the cloud, security becomes paramount. This comprehensive guide covers the latest security best practices for cloud applications in 2024.
Fundamental Security Principles
1. Zero Trust Architecture
Never trust, always verify. Implement strict identity verification for every person and device trying to access resources.
2. Defense in Depth
Layer multiple security controls to protect against various attack vectors.
3. Principle of Least Privilege
Grant users and services only the minimum access required to perform their functions.
Essential Security Measures
Identity and Access Management (IAM)
Implement robust IAM policies with multi-factor authentication and regular access reviews.
Data Encryption
Encrypt data at rest and in transit using industry-standard encryption algorithms.
Network Security
Use VPCs, security groups, and network ACLs to control traffic flow and isolate resources.
Monitoring and Logging
Implement comprehensive logging and real-time monitoring to detect and respond to threats quickly.
Cloud-Specific Considerations
Shared Responsibility Model
Understand what security responsibilities belong to the cloud provider versus your organization.
Configuration Management
Regularly audit and secure cloud service configurations to prevent misconfigurations.
Emerging Threats and Countermeasures
Stay informed about evolving threats like supply chain attacks, API vulnerabilities, and insider threats.
Compliance and Governance
Ensure your cloud security practices align with relevant compliance requirements and industry standards.
Conclusion
Cloud security requires a proactive, multi-layered approach. Regular security assessments, employee training, and staying current with best practices are essential for protecting your cloud applications.